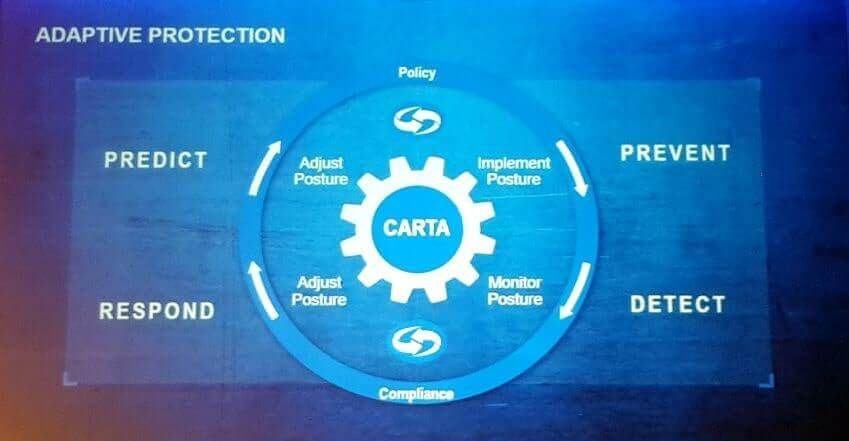
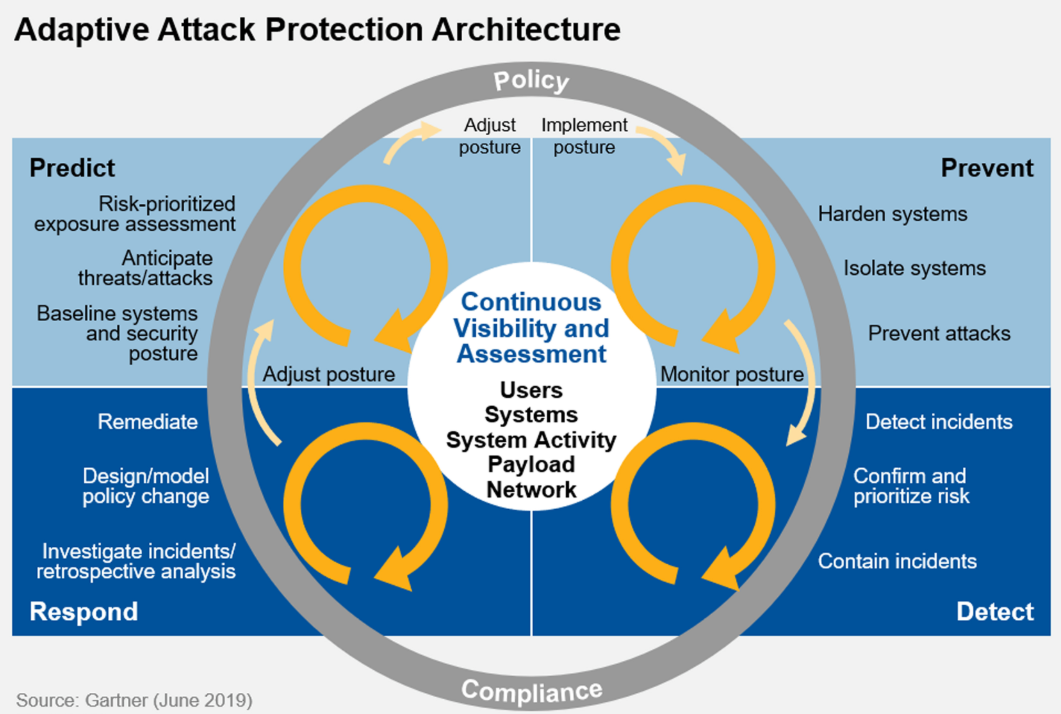
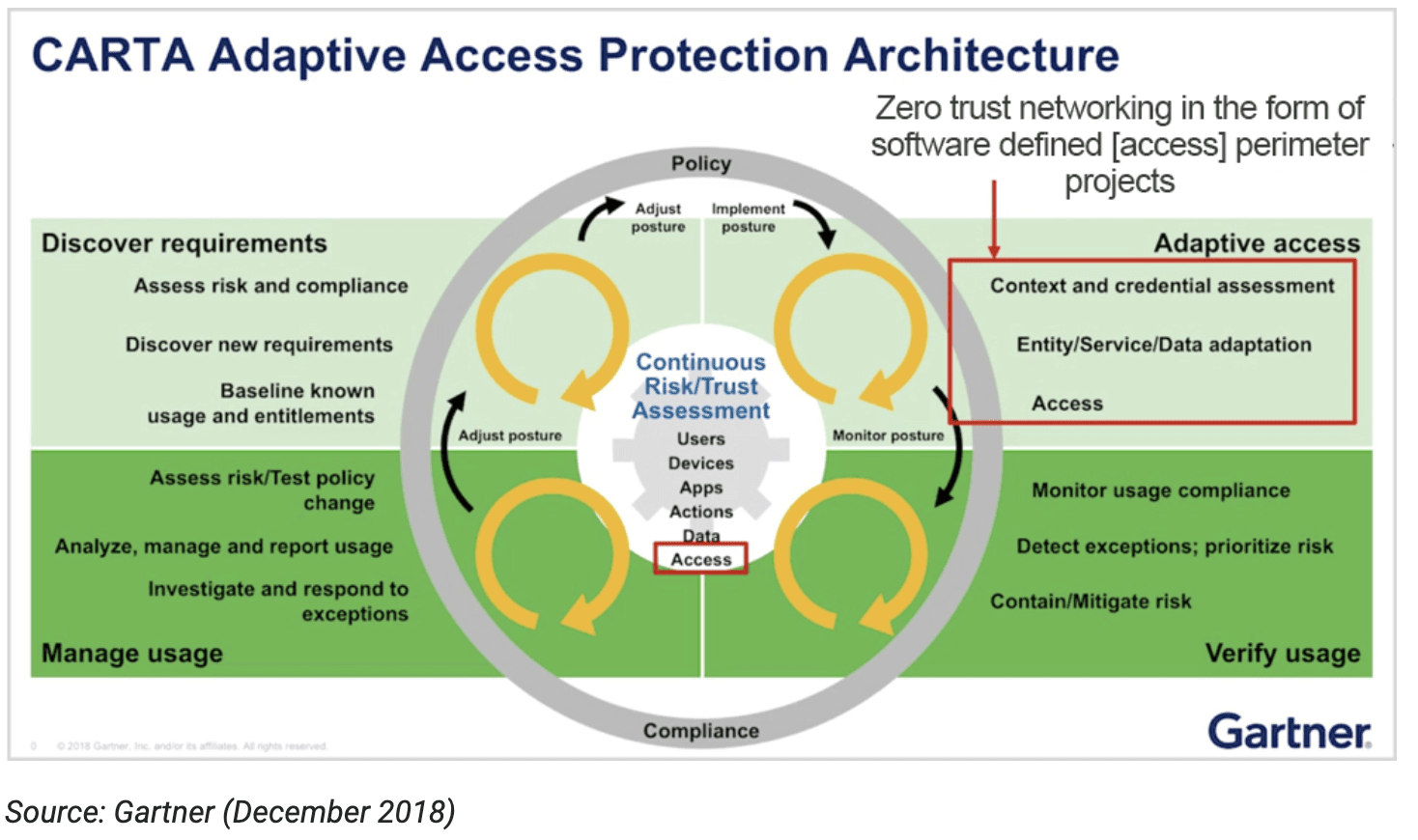
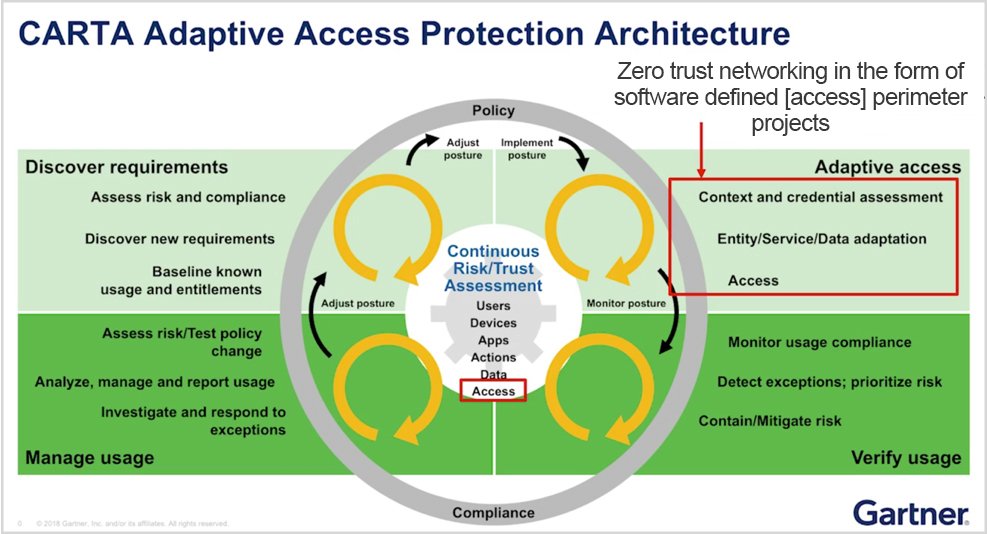
The three main ingredients for the successful implementation of zero trust in the time of COVID-19: Machine learning, carta and software defined perimeter | 2020-09-15 | Security Magazine

Gartner: Seven Imperatives to Adopt a CARTA Strategic Approach - Paperpicks Leading Content Syndication and Distribution Platform