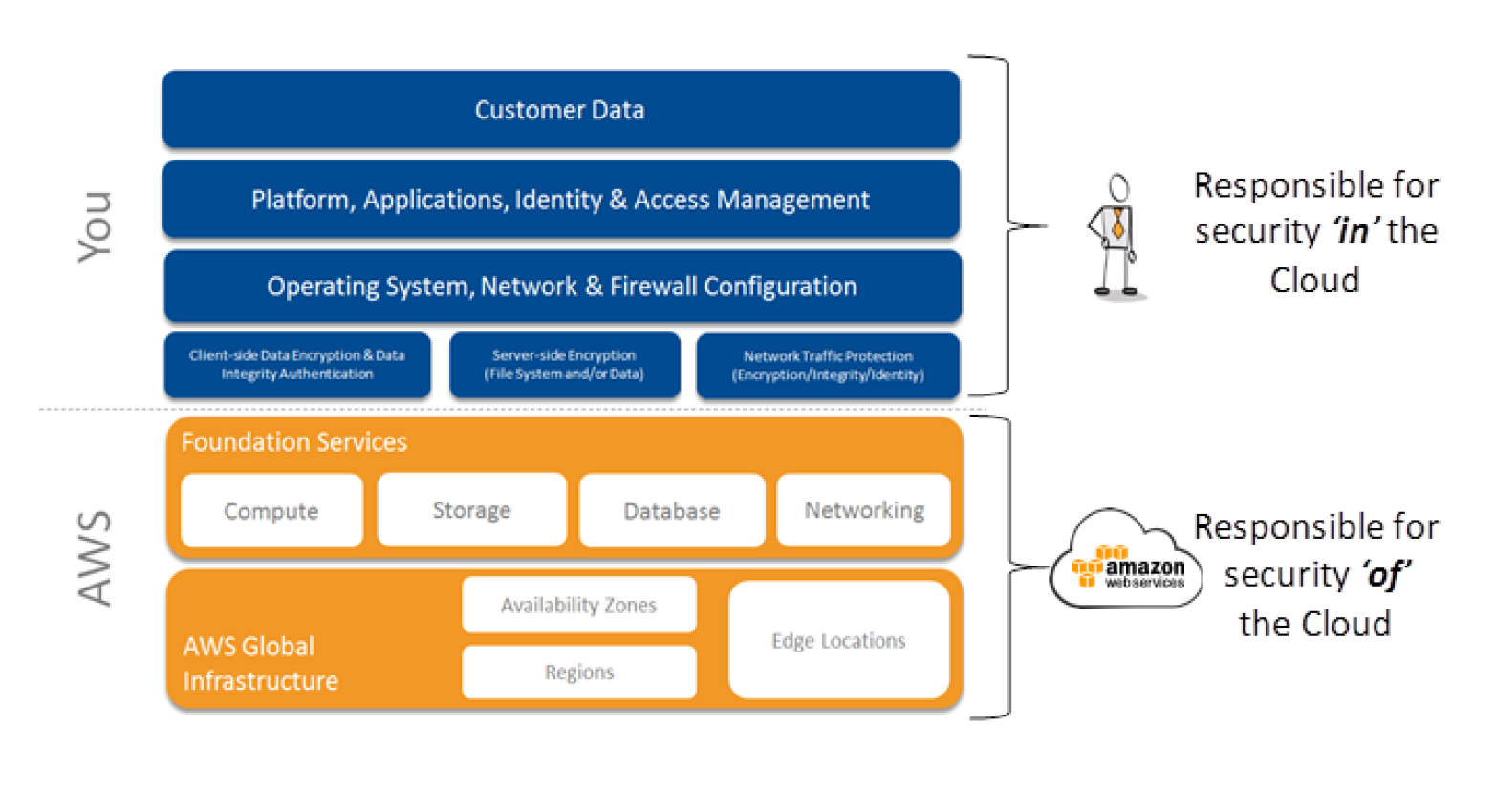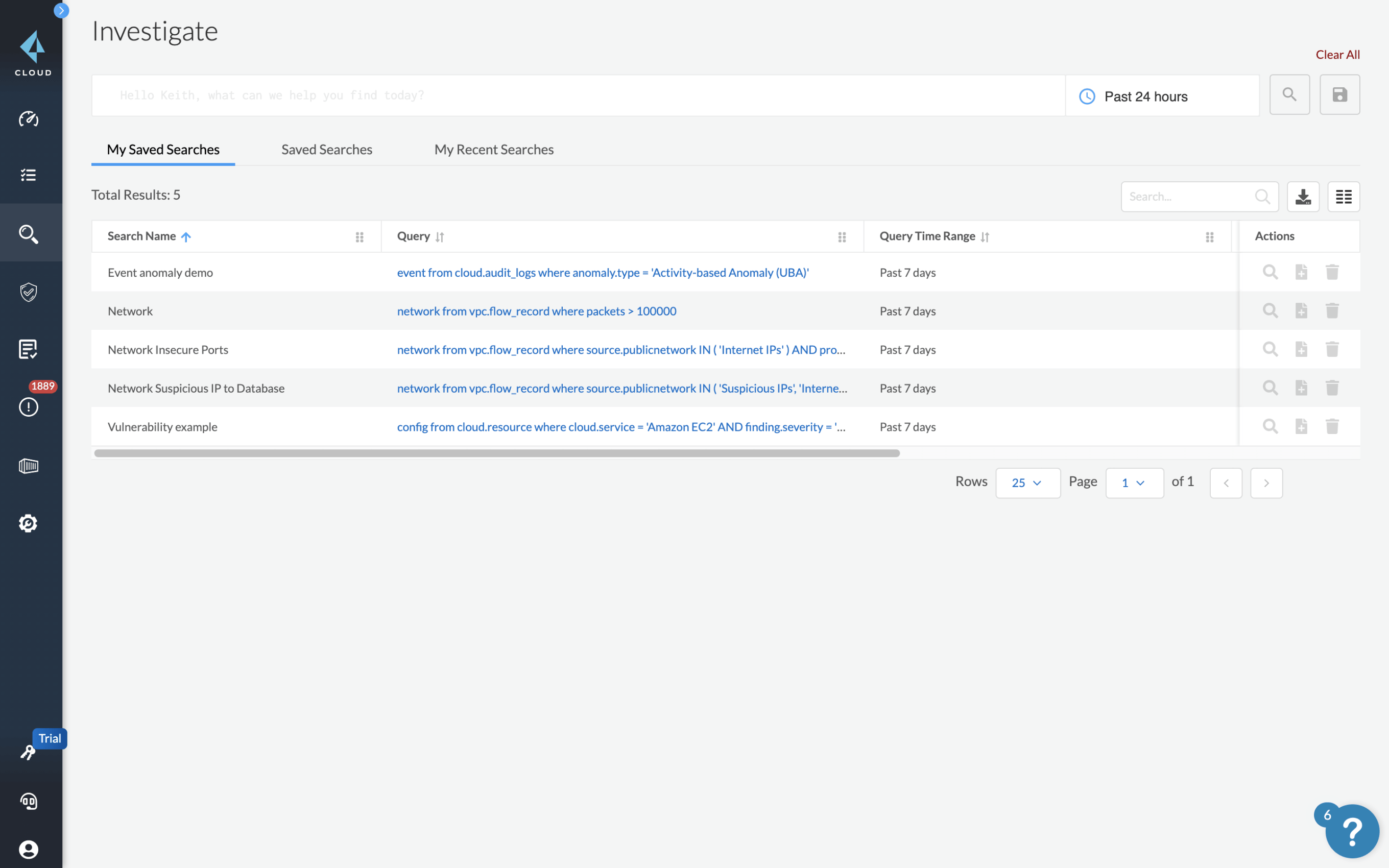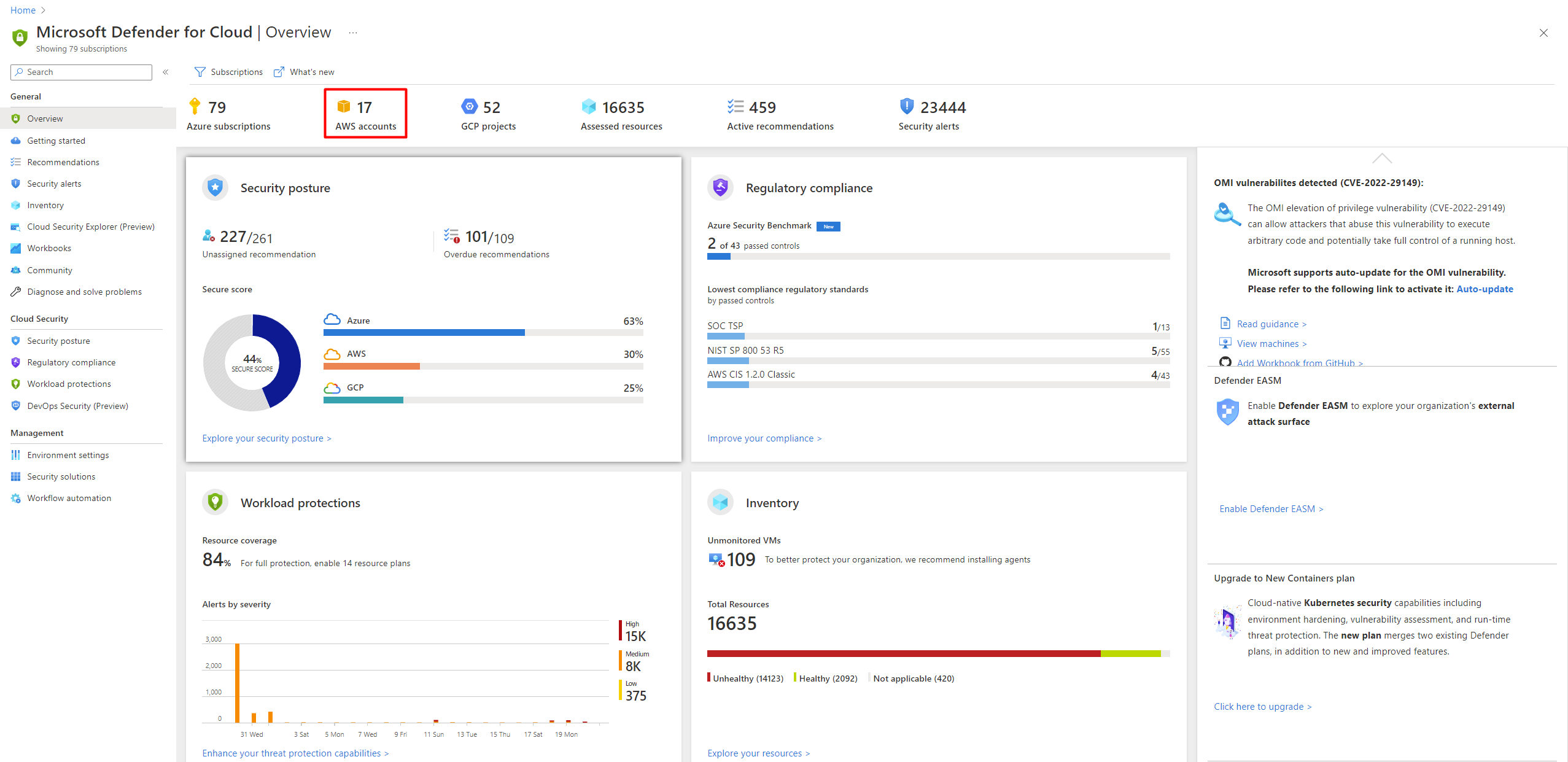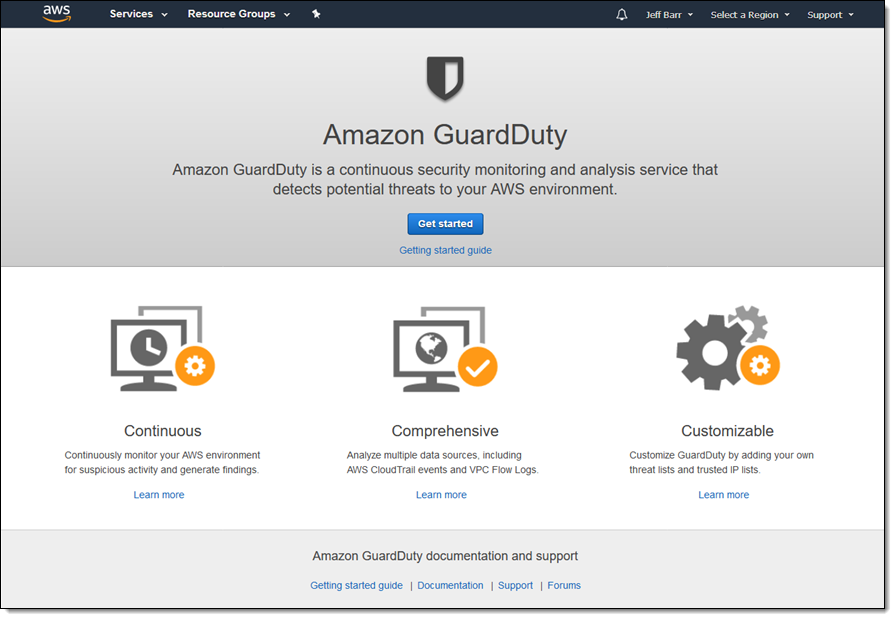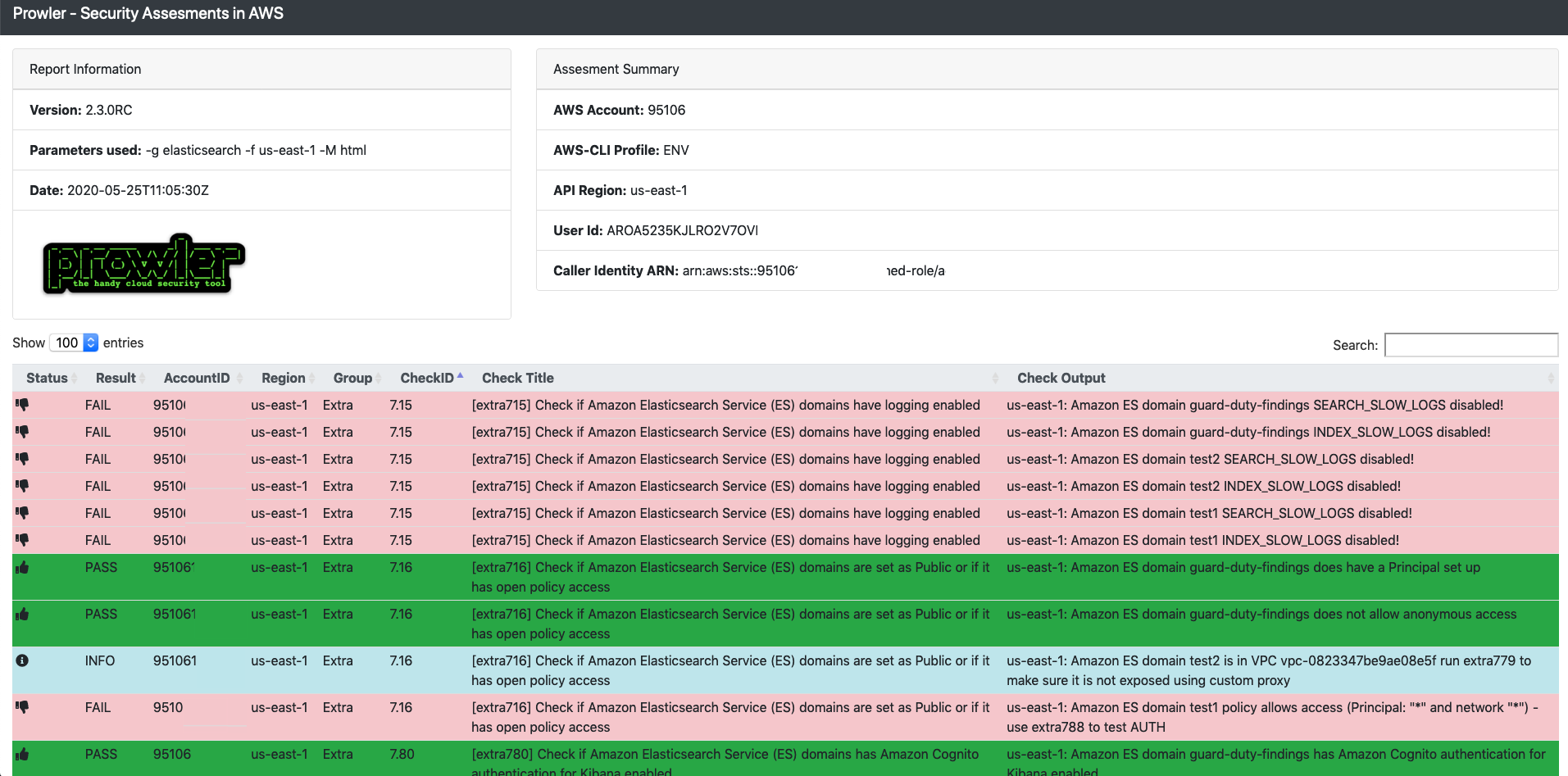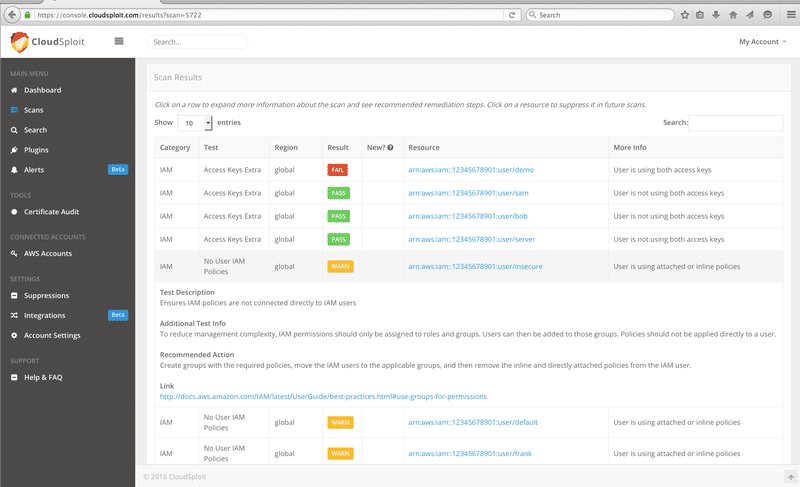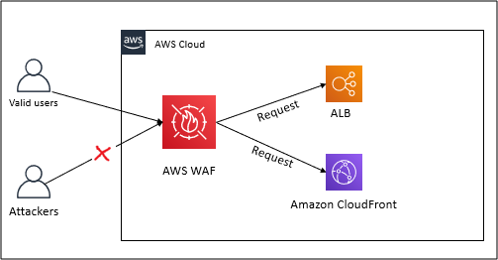
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium
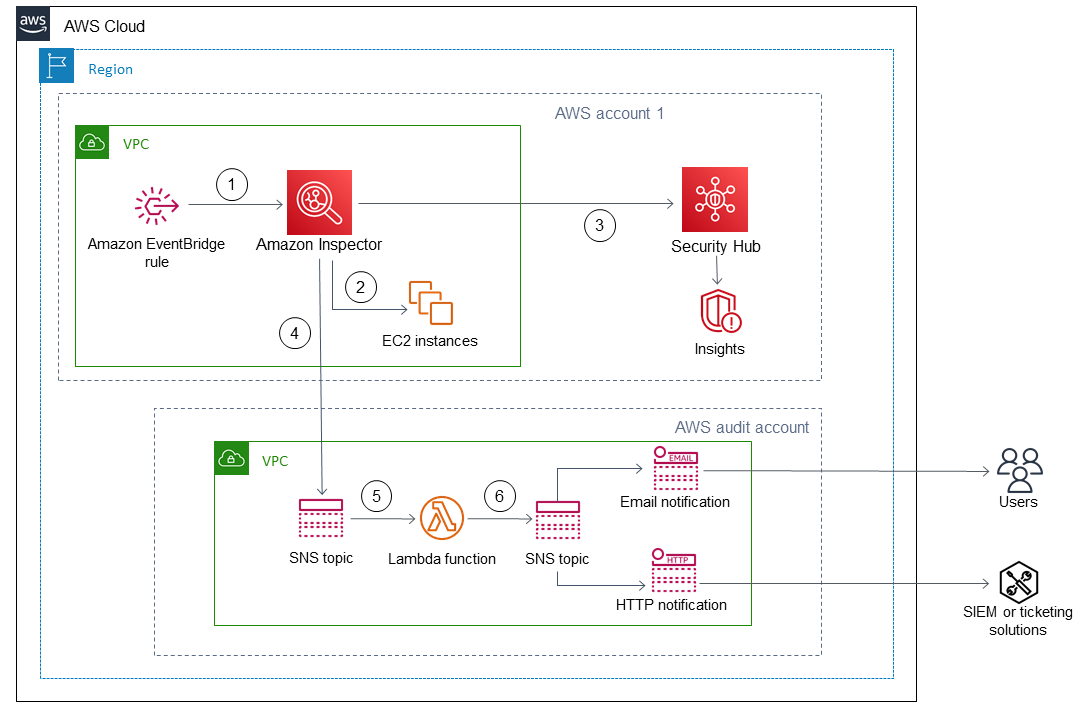
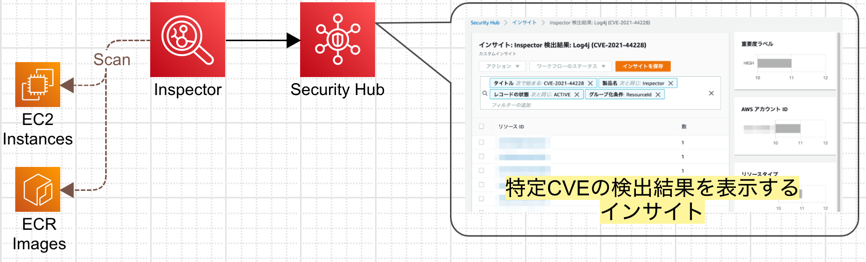
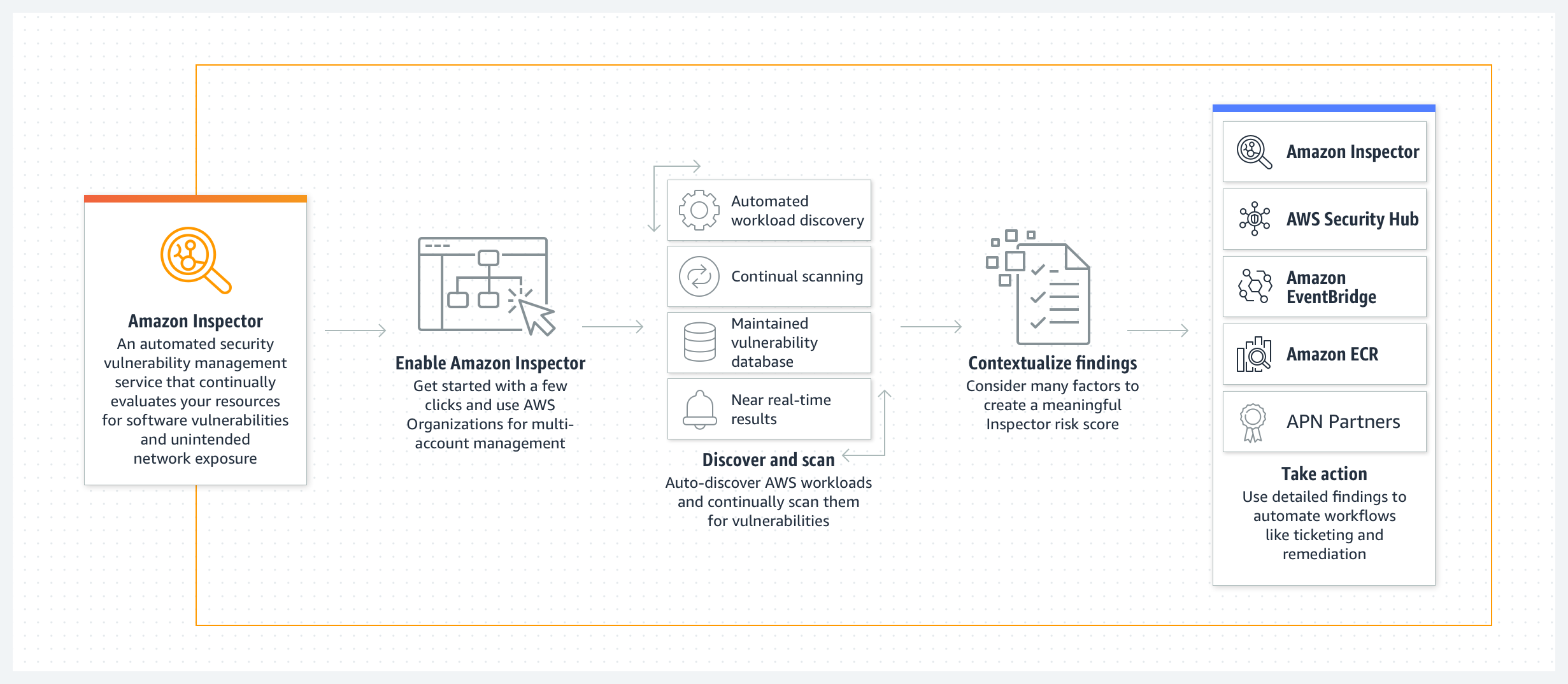
Automate security scans for cross-account workloads using Amazon Inspector and AWS Security Hub - AWS Prescriptive Guidance
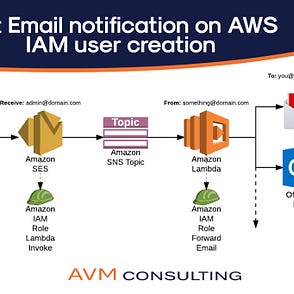
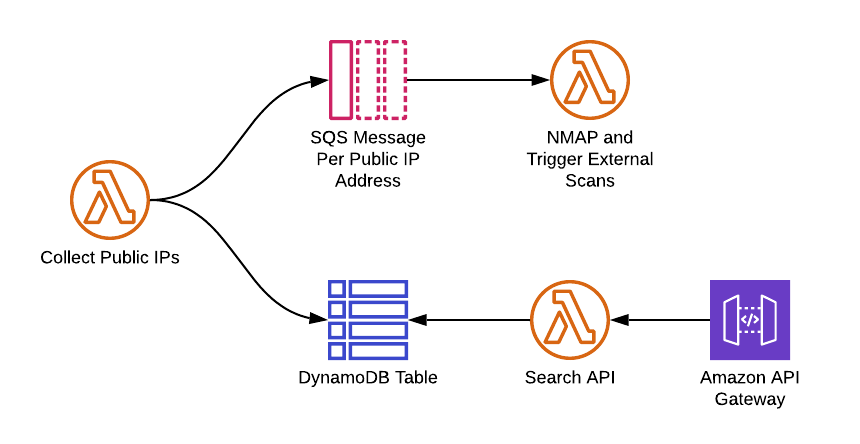
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium